22 Configuring RADIUS Authentication
RADIUS is a client/server security protocol widely used to enable remote authentication and access.
- About Configuring RADIUS Authentication
An Oracle Database network can use any authentication method that supports the RADIUS standard. - RADIUS Components
RADIUS has a set of authentication components that enable you to manage configuration settings. - RADIUS Authentication Modes
User authentication can take place either through synchronous authentication mode or challenge-response (asynchronous) authentication mode. - Enabling RADIUS Authentication, Authorization, and Accounting
To enable RADIUS authentication, authorization, and accounting, you can use Oracle Net Manager. - Using RADIUS to Log in to a Database
You can use RADIUS to log into a database by using either synchronous authentication mode or challenge-response mode. - RSA ACE/Server Configuration Checklist
If you are using an RSA ACE/Server RADIUS server, check the host agent and SecurID tokens for this server before making the initial connection.
Parent topic: Managing Strong Authentication
22.1 About Configuring RADIUS Authentication
An Oracle Database network can use any authentication method that supports the RADIUS standard.
The supported RADIUS standard includes token cards and smart cards when you install and configure the RADIUS protocol. Oracle Database uses RADIUS in a client/server network environment. Moreover, when you use RADIUS, you can change the authentication method without modifying either the Oracle client or the Oracle database server.
From an end user's perspective, the entire authentication process is transparent. When the user seeks access to an Oracle database server, the Oracle database server, acting as the RADIUS client, notifies the RADIUS server. The RADIUS server then:
-
Looks up the user's security information
-
Passes authentication and authorization information between the appropriate authentication server or servers and the Oracle database server
-
Grants the user access to the Oracle database server
-
Logs session information, including when, how often, and for how long the user was connected to the Oracle database server
Note:
Oracle Database does not support RADIUS authentication over database links.
Figure 22-1 illustrates the Oracle Database-RADIUS environment.
Figure 22-1 RADIUS in an Oracle Environment
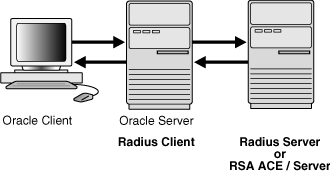
Description of "Figure 22-1 RADIUS in an Oracle Environment"
The Oracle Database server acts as the RADIUS client, passing information between the Oracle client and the RADIUS server. Similarly, the RADIUS server passes information between the Oracle database server and the appropriate authentication servers.
A RADIUS server vendor is often the authentication server vendor as well. In this case authentication can be processed on the RADIUS server. For example, the RSA ACE/Server is both a RADIUS server and an authentication server. It thus authenticates the user's pass code.
Note:
SecurID, an authentication product of RSA Security, Inc., though not directly supported by Oracle Database, has been certified as RADIUS-compliant. You can therefore, run SecurID under RADIUS.
Refer to the RSA Security SecurID documentation for further information.
See Also:
Oracle Database Net Services Reference for information about the sqlnet.ora file
Parent topic: Configuring RADIUS Authentication
22.2 RADIUS Components
RADIUS has a set of authentication components that enable you to manage configuration settings.
Table 22-1 lists the authentication components.
Table 22-1 RADIUS Authentication Components
| Component | Stored Information |
|---|---|
|
Oracle client |
Configuration setting for communicating through RADIUS. |
|
Oracle database server/RADIUS client |
Configuration settings for passing information between the Oracle client and the RADIUS server. The secret key file. |
|
RADIUS server |
Authentication and authorization information for all users. Each client's name or IP address. Each client's shared secret. Unlimited number of menu files enabling users already authenticated to select different login options without reconnecting. |
|
Authentication server or servers |
User authentication information such as pass codes and PINs, depending on the authentication method in use. Note: The RADIUS server can also be the authentication server. |
Parent topic: Configuring RADIUS Authentication
22.3 RADIUS Authentication Modes
User authentication can take place either through synchronous authentication mode or challenge-response (asynchronous) authentication mode.
- Synchronous Authentication Mode
In the synchronous mode, RADIUS lets you use various authentication methods, including passwords and SecurID token cards. - Challenge-Response (Asynchronous) Authentication Mode
When the system uses the asynchronous mode, the user does not need to enter a user name and password at the SQL*Plus CONNECT string.
Parent topic: Configuring RADIUS Authentication
22.3.1 Synchronous Authentication Mode
In the synchronous mode, RADIUS lets you use various authentication methods, including passwords and SecurID token cards.
- Sequence for Synchronous Authentication Mode
The sequence of synchronous authentication mode is comprised of six steps. - Example: Synchronous Authentication with SecurID Token Cards
With SecurID authentication, each user has a token card that displays a dynamic number that changes every sixty seconds.
Parent topic: RADIUS Authentication Modes
22.3.1.1 Sequence for Synchronous Authentication Mode
The sequence of synchronous authentication mode is comprised of six steps.
Figure 22-2 shows the sequence in which synchronous authentication occurs.
Figure 22-2 Synchronous Authentication Sequence
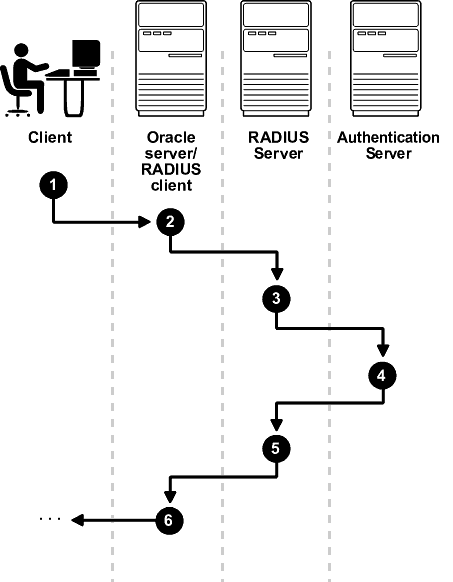
Description of "Figure 22-2 Synchronous Authentication Sequence"
The following steps describe the synchronous authentication sequence:
-
A user logs in by entering a connect string, pass code, or other value. The client system passes this data to the Oracle database server.
-
The Oracle database server, acting as the RADIUS client, passes the data from the Oracle client to the RADIUS server.
-
The RADIUS server passes the data to the appropriate authentication server, such as Smart Card or SecurID ACE for validation.
-
The authentication server sends either an Access Accept or an Access Reject message back to the RADIUS server.
-
The RADIUS server passes this response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client passes the response back to the Oracle client.
Parent topic: Synchronous Authentication Mode
22.3.1.2 Example: Synchronous Authentication with SecurID Token Cards
With SecurID authentication, each user has a token card that displays a dynamic number that changes every sixty seconds.
To gain access to the Oracle database server/RADIUS client, the user enters a valid pass code that includes both a personal identification number (PIN) and the dynamic number currently displayed on the user's SecurID card. The Oracle database server passes this authentication information from the Oracle client to the RADIUS server, which in this case is the authentication server for validation. Once the authentication server (RSA ACE/Server) validates the user, it sends an accept packet to the Oracle database server, which, in turn, passes it to the Oracle client. The user is now authenticated and able to access the appropriate tables and applications.
See Also:
Documentation provided by RSA Security, Inc.
Parent topic: Synchronous Authentication Mode
22.3.2 Challenge-Response (Asynchronous) Authentication Mode
When the system uses the asynchronous mode, the user does not need to enter a user name and password at the SQL*Plus CONNECT string.
- Sequence for Challenge-Response (Asynchronous) Authentication Mode
The sequence for challenge-response (asynchronous) authentication mode is comprised of 12 steps. - Example: Asynchronous Authentication with Smart Cards
With smart card authentication, the user logs in by inserting the smart card into a smart card reader that reads the smart card. - Example: Asynchronous Authentication with ActivCard Tokens
One particular ActivCard token is a hand-held device with a keypad and which displays a dynamic password.
Parent topic: RADIUS Authentication Modes
22.3.2.1 Sequence for Challenge-Response (Asynchronous) Authentication Mode
The sequence for challenge-response (asynchronous) authentication mode is comprised of 12 steps.
Figure 22-3 shows the sequence in which challenge-response (asynchronous) authentication occurs.
Note:
If the RADIUS server is the authentication server, Steps 3, 4, and 5, and Steps 9, 10, and 11 in Figure 22-3 are combined.
Figure 22-3 Asynchronous Authentication Sequence
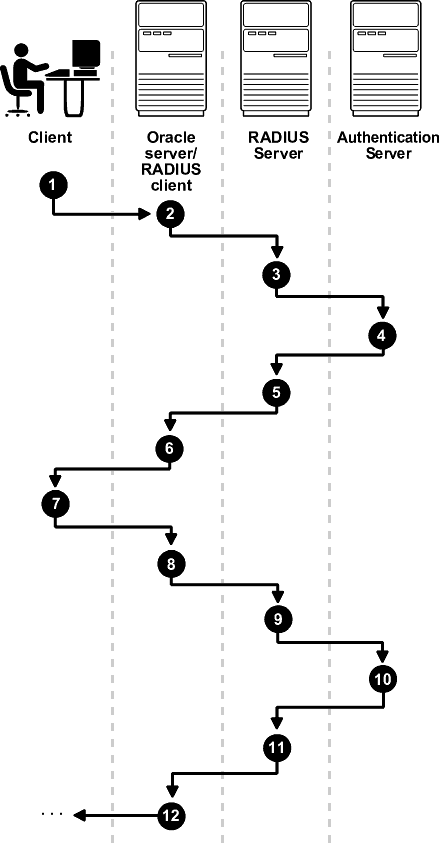
Description of "Figure 22-3 Asynchronous Authentication Sequence"
The following steps describe the asynchronous authentication sequence:
-
A user initiates a connection to an Oracle database server. The client system passes the data to the Oracle database server.
-
The Oracle database server, acting as the RADIUS client, passes the data from the Oracle client to the RADIUS server.
-
The RADIUS server passes the data to the appropriate authentication server, such as a Smart Card, SecurID ACE, or token card server.
-
The authentication server sends a challenge, such as a random number, to the RADIUS server.
-
The RADIUS server passes the challenge to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client, in turn, passes it to the Oracle client. A graphical user interface presents the challenge to the user.
-
The user provides a response to the challenge. To formulate a response, the user can, for example, enter the received challenge into the token card. The token card provides a dynamic password that is entered into the graphical user interface. The Oracle client passes the user's response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client sends the user's response to the RADIUS server.
-
The RADIUS server passes the user's response to the appropriate authentication server for validation.
-
The authentication server sends either an Access Accept or an Access Reject message back to the RADIUS server.
-
The RADIUS server passes the response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client passes the response to the Oracle client.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
22.3.2.2 Example: Asynchronous Authentication with Smart Cards
With smart card authentication, the user logs in by inserting the smart card into a smart card reader that reads the smart card.
The smart card is a plastic card, like a credit card, with an embedded integrated circuit for storing information.
The Oracle client sends the login information contained in the smart card to the authentication server by way of the Oracle database server/RADIUS client and the RADIUS server. The authentication server sends back a challenge to the Oracle client, by way of the RADIUS server and the Oracle database server, prompting the user for authentication information. The information could be, for example, a PIN as well as additional authentication information contained on the smart card.
The Oracle client sends the user's response to the authentication server by way of the Oracle database server and the RADIUS server. If the user has entered a valid number, the authentication server sends an accept packet back to the Oracle client by way of the RADIUS server and the Oracle database server. The user is now authenticated and authorized to access the appropriate tables and applications. If the user has entered incorrect information, the authentication server sends back a message rejecting user's access.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
22.3.2.3 Example: Asynchronous Authentication with ActivCard Tokens
One particular ActivCard token is a hand-held device with a keypad and which displays a dynamic password.
When the user seeks access to an Oracle database server by entering a password, the information is passed to the appropriate authentication server by way of the Oracle database server/RADIUS client and the RADIUS server. The authentication server sends back a challenge to the client, by way of the RADIUS server and the Oracle database server. The user types that challenge into the token, and the token displays a number for the user to send in response.
The Oracle client then sends the user's response to the authentication server by way of the Oracle database server and the RADIUS server. If the user has typed a valid number, the authentication server sends an accept packet back to the Oracle client by way of the RADIUS server and the Oracle database server. The user is now authenticated and authorized to access the appropriate tables and applications. If the user has entered an incorrect response, the authentication server sends back a message rejecting the user's access.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
22.4 Enabling RADIUS Authentication, Authorization, and Accounting
To enable RADIUS authentication, authorization, and accounting, you can use Oracle Net Manager.
- Step 1: Configure RADIUS Authentication
To configure RADIUS authentication, you must first configure it on the Oracle client, then the server. Afterward, you can configure additional RADIUS features. - Step 2: Create a User and Grant Access
After you complete the RADIUS authentication, you must create an Oracle Database user who for the RADIUS configuration. - Step 3: Configure External RADIUS Authorization (Optional)
You must configure the Oracle server, the Oracle client, and the RADIUS server to RADIUS users who must connect to an Oracle database. - Step 4: Configure RADIUS Accounting
RADIUS accounting logs information about access to the Oracle database server and stores it in a file on the RADIUS accounting server. - Step 5: Add the RADIUS Client Name to the RADIUS Server Database
The RADIUS server that you select must comply with RADIUS standards. - Step 6: Configure the Authentication Server for Use with RADIUS
After you add the RADIUS client name to the RADIUS server database, you can configure the authentication server to use the RADIUS. - Step 7: Configure the RADIUS Server for Use with the Authentication Server
After you configure the authentication server for use with RADIUS, you can configure the RADIUS server to use the authentication server. - Step 8: Configure Mapping Roles
If the RADIUS server supports vendor type attributes, then you can manage roles by storing them in the RADIUS server.
Parent topic: Configuring RADIUS Authentication
22.4.1 Step 1: Configure RADIUS Authentication
To configure RADIUS authentication, you must first configure it on the Oracle client, then the server. Afterward, you can configure additional RADIUS features.
Note:
Unless otherwise indicated, perform these configuration tasks by using Oracle Net Manager or by using any text editor to modify the sqlnet.ora file. Be aware that in a multitenant environment, the settings in the sqlnet.ora file apply to all pluggable databases (PDBs).
- Step 1A: Configure RADIUS on the Oracle Client
You can use Oracle Net Manager to configure RADIUS on the Oracle client. - Step 1B: Configure RADIUS on the Oracle Database Server
You must create a file to hold the RADIUS key and store this file on the Oracle database server. Then you must configure the appropriate parameters in thesqlnet.orafile. - Step 1C: Configure Additional RADIUS Features
You can change the default settings, configure the challenge-response mode, and set parameters for an alternate RADIUS server.
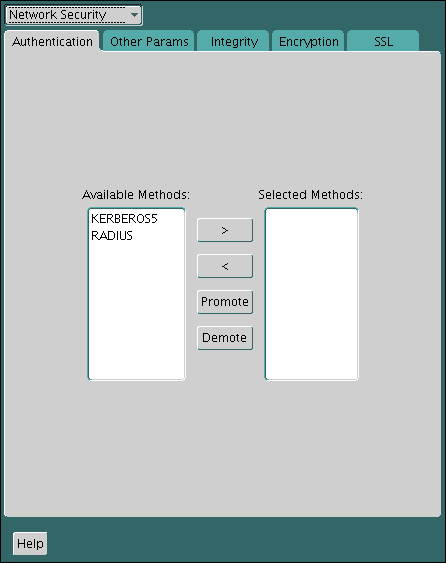
22.4.1.1 Step 1A: Configure RADIUS on the Oracle Client
You can use Oracle Net Manager to configure RADIUS on the Oracle client.
-
Start Oracle Net Manager.
-
(UNIX) From
$ORACLE_HOME/bin, enter the following command at the command line:netmgr
-
(Windows) Select Start, Programs, Oracle - HOME_NAME, Configuration and Migration Tools, then Net Manager.
-
-
Expand Oracle Net Configuration, and from Local, select Profile.
-
From the Naming list, select Network Security.
The Network Security tabbed window appears.
-
Select the Authentication tab. (It should be selected by default.)
-
From the Available Methods list, select RADIUS.
-
Select the right-arrow (>) to move RADIUS to the Selected Methods list.
Move any other methods you want to use in the same way.
-
Arrange the selected methods in order of required usage by selecting a method in the Selected Methods list, and clicking Promote or Demote to position it in the list.
For example, put RADIUS at the top of the list for it to be the first service used.
-
From the File menu, select Save Network Configuration.
The
sqlnet.orafile is updated with the following entry:SQLNET.AUTHENTICATION_SERVICES=(RADIUS)
Parent topic: Step 1: Configure RADIUS Authentication
22.4.1.2 Step 1B: Configure RADIUS on the Oracle Database Server
You must create a file to hold the RADIUS key and store this file on the Oracle database server. Then you must configure the appropriate parameters in the sqlnet.ora file.
- Step 1B (1): Create the RADIUS Secret Key File on the Oracle Database Server
First, you must create the RADIUS secret key file. - Step 1B (2): Configure RADIUS Parameters on the Server (sqlnet.ora file)
After you create RADIUS secret key file, you are ready to configure the appropriate parameters in thesqlnet.orafile. - Step 1B (3): Set Oracle Database Server Initialization Parameters
After you configure the sqlnet.ora file, you must configure theinit.orainitialization file.
Parent topic: Step 1: Configure RADIUS Authentication
22.4.1.2.1 Step 1B (1): Create the RADIUS Secret Key File on the Oracle Database Server
First, you must create the RADIUS secret key file.
-
Obtain the RADIUS secret key from the RADIUS server.
For each RADIUS client, the administrator of the RADIUS server creates a shared secret key, which must be less than or equal to 16 characters.
-
On the Oracle database server, create a directory:
-
(UNIX)
$ORACLE_HOME/network/security -
(Windows)
ORACLE_BASE\ORACLE_HOME\network\security
-
-
Create the file
radius.keyto hold the shared secret copied from the RADIUS server. Place the file in the directory you created in Step 2. -
Copy the shared secret key and paste it (and nothing else) into the
radius.keyfile created on the Oracle database server. -
For security purposes, change the file permission of
radius.keyto read only, accessible only by the Oracle owner.Oracle relies on the file system to keep this file secret.
See Also:
The RADIUS server administration documentation, for information about obtaining the secret key
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
22.4.1.2.2 Step 1B (2): Configure RADIUS Parameters on the Server (sqlnet.ora file)
After you create RADIUS secret key file, you are ready to configure the appropriate parameters in the sqlnet.ora file.
-
Start Oracle Net Manager.
-
(UNIX) From
$ORACLE_HOME/bin, enter the following command at the command line:netmgr
-
(Windows) Select Start, Programs, Oracle - HOME_NAME, Configuration and Migration Tools, then Net Manager.
-
-
Expand Oracle Net Configuration, and from Local, select Profile.
-
From the Naming list, select Network Security.
The Network Security tabbed window appears.
-
Select the Authentication tab.
-
From the Available Methods list, select RADIUS.
-
Move RADIUS to the Selected Methods list by choosing the right-arrow (>).
-
To arrange the selected methods in order of desired use, select a method in the Selected Methods list, and select Promote or Demote to position it in the list.
For example, if you want RADIUS to be the first service used, then put it at the top of the list.
-
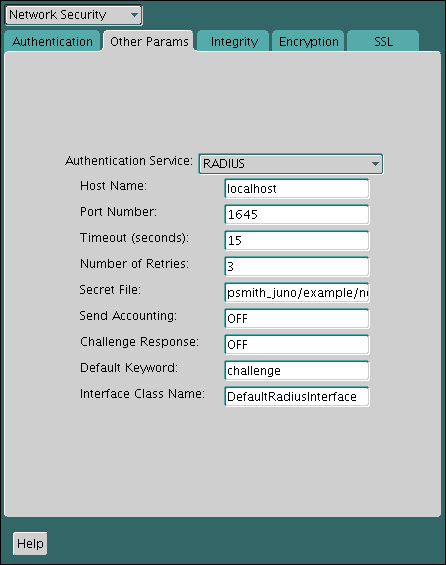
Select the Other Params tab.
-
From the Authentication Service list, select RADIUS.
-
In the Host Name field, accept the localhost as the default primary RADIUS server, or enter another host name.
-
Ensure that the default value of the Secret File field is valid.
-
From the File menu, select Save Network Configuration.
The
sqlnet.orafile is updated with the following entries:SQLNET.AUTHENTICATION_SERVICES=RADIUS SQLNET.RADIUS_AUTHENTICATION=RADIUS_server_{hostname|IP_address}Note:
The
IP_addresscan either be an Internet Protocol Version 4 (IPv4) or Internet Protocol Version 6 (IPv6) address. The RADIUS adapter supports both IPv4 and IPv6 based servers.
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
22.4.1.2.3 Step 1B (3): Set Oracle Database Server Initialization Parameters
After you configure the sqlnet.ora file, you must configure the init.ora initialization file.
-
Add the following setting to the
init.orafile.OS_AUTHENT_PREFIX=""
By default, the
init.orafile is located in theORACLE_HOME/dbsdirectory (or the same location of the data files) on Linux and UNIX systems, and in theORACLE_HOME\databasedirectory on Windows. -
Restart the database.
For example:
SQL> SHUTDOWN SQL> STARTUP
See Also:
Oracle Database Reference for information about setting initialization parameters
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
22.4.1.3 Step 1C: Configure Additional RADIUS Features
You can change the default settings, configure the challenge-response mode, and set parameters for an alternate RADIUS server.
- Step 1C(1): Change Default Settings
You can use Oracle Net Manager to change the default RADIUS settings. - Step 1C(2): Configure Challenge-Response Mode
To configure challenge-response mode, you must specify information such as a dynamic password that you obtain from a token card. - Step 1C(3): Set Parameters for an Alternate RADIUS Server
If you are using an alternate RADIUS server, then you must set additional parameters.
Parent topic: Step 1: Configure RADIUS Authentication
22.4.1.3.1 Step 1C(1): Change Default Settings
You can use Oracle Net Manager to change the default RADIUS settings.
-
Start Oracle Net Manager.
-
(UNIX) From
$ORACLE_HOME/bin, enter the following command at the command line:netmgr
-
(Windows) Select Start, Programs, Oracle - HOME_NAME, Configuration and Migration Tools, then Net Manager.
-
-
Expand Oracle Net Configuration, and from Local, select Profile.
-
From the Naming list, select Network Security.
The Network Security tabbed window appears.
-
Click the Other Params tab.
-
From the Authentication Service list, select RADIUS.
-
Change the default setting for any of the following fields:
-
Port Number: Specifies the listening port of the primary RADIUS server. The default value is 1645.
-
Timeout (seconds): Specifies the time the Oracle database server waits for a response from the primary RADIUS server. The default is 15 seconds.
-
Number of Retries: Specifies the number of times the Oracle database server resends messages to the primary RADIUS server. The default is three retries. For instructions on configuring RADIUS accounting, see Step 4: Configure RADIUS Accounting.
-
Secret File: Specifies the location of the secret key on the Oracle database server. The field specifies the location of the secret key file, not the secret key itself. For information about specifying the secret key, see Step 1B (1): Create the RADIUS Secret Key File on the Oracle Database Server.
-
-
From the File menu, select Save Network Configuration.
The
sqlnet.orafile is updated with the following entries:SQLNET.RADIUS_AUTHENTICATION_PORT=(PORT) SQLNET.RADIUS_AUTHENTICATION_TIMEOUT=(NUMBER OF SECONDS TO WAIT FOR response) SQLNET.RADIUS_AUTHENTICATION_RETRIES=(NUMBER OF TIMES TO RE-SEND TO RADIUS server) SQLNET.RADIUS_SECRET=(path/radius.key)
Parent topic: Step 1C: Configure Additional RADIUS Features
22.4.1.3.2 Step 1C(2): Configure Challenge-Response Mode
To configure challenge-response mode, you must specify information such as a dynamic password that you obtain from a token card.
With the RADIUS adapter, this interface is Java-based to provide optimal platform independence.
Note:
Third party vendors of authentication devices must customize this graphical user interface to fit their particular device. For example, a smart card vendor would customize the Java interface so that the Oracle client reads data, such as a dynamic password, from the smart card. When the smart card receives a challenge, it responds by prompting the user for more information, such as a PIN.
To configure challenge-response mode:
-
If you are using JDK 1.1.7 or JRE 1.1.7, then set the
JAVA_HOMEenvironment variable to the JRE or JDK location on the system where the Oracle client is run:-
On UNIX, enter this command at the prompt:
% setenv JAVA_HOME /usr/local/packages/jre1.1.7B
-
On Windows, select Start, Settings, Control Panel, System, Environment, and set the
JAVA_HOMEvariable as follows:c:\java\jre1.1.7B
This step is not required for any other JDK/JRE version.
-
-
Start Oracle Net Manager.
-
(UNIX) From
$ORACLE_HOME/bin, enter the following command at the command line:netmgr
-
(Windows) Select Start, Programs, Oracle - HOME_NAME, Configuration and Migration Tools, then Net Manager.
-
-
Expand Oracle Net Configuration, and from Local, select Profile.
-
From the Naming list, select Network Security.
The Network Security tabbed window appears.
-
From the Authentication Service list, select RADIUS.
-
In the Challenge Response field, enter ON to enable challenge-response.
-
In the Default Keyword field, accept the default value of the challenge or enter a keyword for requesting a challenge from the RADIUS server.
The keyword feature is provided by Oracle and supported by some, but not all, RADIUS servers. You can use this feature only if your RADIUS server supports it.
By setting a keyword, you let the user avoid using a password to verify identity. If the user does not enter a password, the keyword you set here is passed to the RADIUS server which responds with a challenge requesting, for example, a driver's license number or birth date. If the user does enter a password, the RADIUS server may or may not respond with a challenge, depending upon the configuration of the RADIUS server.
-
In the Interface Class Name field, accept the default value of DefaultRadiusInterface or enter the name of the class you have created to handle the challenge-response conversation.
If other than the default RADIUS interface is used, then you also must edit the
sqlnet.orafile to enterSQLNET.RADIUS_CLASSPATH=(location), wherelocationis the complete path name of the jar file. It defaults to$ORACLE_HOME/network/jlib/netradius.jar:$ORACLE_HOME/JRE/lib/vt.jar -
From the File menu, select Save Network Configuration.
The
sqlnet.orafile is updated with the following entries:SQLNET.RADIUS_CHALLENGE_RESPONSE=([ON | OFF]) SQLNET.RADIUS_CHALLENGE_KEYWORD=(KEYWORD) SQLNET.RADIUS_AUTHENTICATION_INTERFACE=(name of interface including the package name delimited by "/" for ".")
See Also:
Integrating Authentication Devices Using RADIUS for information about how to customize the challenge-response user interface
Parent topic: Step 1C: Configure Additional RADIUS Features
22.4.1.3.3 Step 1C(3): Set Parameters for an Alternate RADIUS Server
If you are using an alternate RADIUS server, then you must set additional parameters.
-
Set the following parameters in the
sqlnet.orafile:SQLNET.RADIUS_ALTERNATE=(hostname or ip address of alternate radius server) SQLNET.RADIUS_ALTERNATE_PORT=(1812) SQLNET.RADIUS_ALTERNATE_TIMEOUT=(number of seconds to wait for response) SQLNET.RADIUS_ALTERNATE_RETRIES=(number of times to re-send to radius server)
Parent topic: Step 1C: Configure Additional RADIUS Features
22.4.2 Step 2: Create a User and Grant Access
After you complete the RADIUS authentication, you must create an Oracle Database user who for the RADIUS configuration.
-
Start SQL*Plus and then execute these statements to create and grant access to a user identified externally on the Oracle database server.
CONNECT system@database_name; Enter password: password CREATE USER username IDENTIFIED EXTERNALLY; GRANT CREATE SESSION TO USER username; EXIT
If you are using Windows, you can use the Security Manager tool in Oracle Enterprise Manager.
-
Enter the same
usernamein the RADIUS server's users file.
See Also:
Administration documentation for the RADIUS server
22.4.3 Step 3: Configure External RADIUS Authorization (Optional)
You must configure the Oracle server, the Oracle client, and the RADIUS server to RADIUS users who must connect to an Oracle database.
- Step 3A: Configure the Oracle Server (RADIUS Client)
You can edit theinit.orafile to configure an Oracle server for a RADIUS client. - Step 3B: Configure the Oracle Client Where Users Log In
Next, you must configure the Oracle client where users log in. - Step 3C: Configure the RADIUS Server
To configure the RADIUS server, you must modify the RADIUS server attribute configuration file.
22.4.3.1 Step 3A: Configure the Oracle Server (RADIUS Client)
You can edit the init.ora file to configure an Oracle server for a RADIUS client.
To do so, you must modify the init.ora file, restart the database, and the set the RADIUS challenge-response mode.
-
Add the
OS_ROLESparameter to theinit.orafile and set this parameter toTRUEas follows:OS_ROLES=TRUE
By default, the
init.orafile is located in theORACLE_HOME/dbsdirectory (or the same location of the data files) on Linux and UNIX systems, and in theORACLE_HOME\databasedirectory on Windows. -
Restart the database so that the system can read the change to the
init.orafile.For example:
SQL> SHUTDOWN SQL> STARTUP
-
Set the RADIUS challenge-response mode to
ONfor the server if you have not already done so by following the steps listed in Step 1C(2): Configure Challenge-Response Mode. -
Add externally identified users and roles.
22.4.3.2 Step 3B: Configure the Oracle Client Where Users Log In
Next, you must configure the Oracle client where users log in.
-
Set the RADIUS challenge-response mode to
ONfor the client if you have not already done so by following the steps listed in Step 1C(2): Configure Challenge-Response Mode.
22.4.3.3 Step 3C: Configure the RADIUS Server
To configure the RADIUS server, you must modify the RADIUS server attribute configuration file.
-
Add the following attributes to the RADIUS server attribute configuration file:
ATTRIBUTE NAME CODE TYPE VENDOR_SPECIFIC26
Integer
ORACLE_ROLE1
String
-
Assign a Vendor ID for Oracle in the RADIUS server attribute configuration file that includes the SMI Network Management Private Enterprise Code of
111.For example, enter the following in the RADIUS server attribute configuration file:
VALUE VENDOR_SPECIFIC ORACLE 111 -
Using the following syntax, add the
ORACLE_ROLEattribute to the user profile of the users who will use external RADIUS authorization:ORA_databaseSID_rolename[_[A]|[D]]In this specification.:
-
ORAdesignates that this role is used for Oracle purposes -
databaseSIDis the Oracle system identifier that is configured in the databaseinit.orafile.By default, the
init.orafile is located in theORACLE_HOME/dbsdirectory (or the same location of the data files) on Linux and UNIX systems, and in theORACLE_HOME\databasedirectory on Windows. -
rolenameis the name of role as it is defined in the data dictionary. -
Ais an optional character that indicates the user has administrator's privileges for this role. -
Dis an optional character that indicates this role is to be enabled by default.
Ensure that RADIUS groups that map to Oracle roles adhere to the
ORACLE_ROLEsyntax.For example:
USERNAME USERPASSWD="user_password", SERVICE_TYPE=login_user, VENDOR_SPECIFIC=ORACLE, ORACLE_ROLE=ORA_ora920_sysdbaSee Also:
The RADIUS server administration documentation for information about configuring the server.
-
22.4.4 Step 4: Configure RADIUS Accounting
RADIUS accounting logs information about access to the Oracle database server and stores it in a file on the RADIUS accounting server.
Use this feature only if both the RADIUS server and authentication server support it.
- Step 4A: Set RADIUS Accounting on the Oracle Database Server
To set RADIUS accounting on the server, you can use Oracle Net Manager. - Step 4B: Configure the RADIUS Accounting Server
RADIUS Accounting Server resides on the same host as the RADIUS authentication server or on a separate host.
22.4.4.1 Step 4A: Set RADIUS Accounting on the Oracle Database Server
To set RADIUS accounting on the server, you can use Oracle Net Manager.
-
Start Oracle Net Manager.
-
(UNIX) From
$ORACLE_HOME/bin, enter the following command at the command line:netmgr
-
(Windows) Select Start, Programs, Oracle - HOME_NAME, Configuration and Migration Tools, then Net Manager.
-
-
Expand Oracle Net Configuration, and from Local, select Profile.
-
From the Naming list, select Network Security.
The Network Security tabbed window appears.
-
Select the Other Params tab.
-
From the Authentication Service list, select RADIUS.
-
In the Send Accounting field, enter ON to enable accounting or OFF to disable accounting.
-
From the File menu, select Save Network Configuration.
The
sqlnet.orafile is updated with the following entry:SQLNET.RADIUS_SEND_ACCOUNTING= ON
Parent topic: Step 4: Configure RADIUS Accounting
22.4.4.2 Step 4B: Configure the RADIUS Accounting Server
RADIUS Accounting Server resides on the same host as the RADIUS authentication server or on a separate host.
-
See the administration documentation for the RADIUS server, for information about configuring RADIUS accounting.
Parent topic: Step 4: Configure RADIUS Accounting
22.4.5 Step 5: Add the RADIUS Client Name to the RADIUS Server Database
The RADIUS server that you select must comply with RADIUS standards.
You can use any RADIUS server that complies with the Internet Engineering Task Force (IETF) RFC #2138, Remote Authentication Dial In User Service (RADIUS), and RFC #2139 RADIUS Accounting standards. Because RADIUS servers vary, consult the documentation for your particular RADIUS server for any unique interoperability requirements.
To add the RADIUS client name to a Livingston RADIUS server:
-
Open the clients file, which is located in
/etc/raddb/clients.The following text and table appear:
@ (#) clients 1.1 2/21/96 Copyright 1991 Livingston Enterprises Inc This file contains a list of clients which are allowed to make authentication requests and their encryption key. The first field is a valid hostname. The second field (separated by blanks or tabs) is the encryption key. Client Name Key
-
In the
CLIENT NAMEcolumn, enter the host name or IP address of the host on which the Oracle database server is running.In the
KEYcolumn, type the shared secret.The value you enter in the
CLIENT NAMEcolumn, whether it is the client's name or IP address, depends on the RADIUS server. -
Save and close the clients file.
See Also:
Administration documentation for the RADIUS server
22.4.6 Step 6: Configure the Authentication Server for Use with RADIUS
After you add the RADIUS client name to the RADIUS server database, you can configure the authentication server to use the RADIUS.
-
Refer to the authentication server documentation for instructions about configuring the authentication servers.
22.4.7 Step 7: Configure the RADIUS Server for Use with the Authentication Server
After you configure the authentication server for use with RADIUS, you can configure the RADIUS server to use the authentication server.
-
Refer to the RADIUS server documentation for instructions about configuring the RADIUS server for use with the authentication server.
22.4.8 Step 8: Configure Mapping Roles
If the RADIUS server supports vendor type attributes, then you can manage roles by storing them in the RADIUS server.
The Oracle database server downloads the roles when there is a CONNECT request using RADIUS.To use this feature, you must configure roles on both the Oracle database server and the RADIUS server.
-
Use a text editor to set the
OS_ROLESparameter in the initialization parameters file on the Oracle database server.By default, the
init.orafile is located in theORACLE_HOME/dbsdirectory (or the same location of the data files) on Linux and UNIX systems, and in theORACLE_HOME\databasedirectory on Windows. -
Stop and restart the Oracle database server.
For example:
SHUTDOWN STARTUP
-
Create each role that the RADIUS server will manage on the Oracle database server with the value
IDENTIFIED EXTERNALLY.To configure roles on the RADIUS server, use the following syntax:
ORA_DatabaseName.DatabaseDomainName_RoleName
In this specification:
-
DatabaseNameis the name of the Oracle database server for which the role is being created. This is the same as the value of the DB_NAME initialization parameter. -
DatabaseDomainNameis the name of the domain to which the Oracle database server belongs. The value is the same as the value of theDB_DOMAINinitialization parameter. -
RoleNameis name of the role created in the Oracle database server.
For example:
ORA_USERDB.US.EXAMPLE.COM_MANAGER
-
-
Configure RADIUS challenge-response mode.
22.5 Using RADIUS to Log in to a Database
You can use RADIUS to log into a database by using either synchronous authentication mode or challenge-response mode.
-
Start SQL*Plus and use one of the following ways to log in to the database:
-
If you are using the synchronous authentication mode, first ensure that challenge-response mode is not turned to
ON, and then enter the following command:CONNECT username@database_alias Enter password: password
-
If you are using the challenge-response mode, ensure that challenge-response mode is set to
ONand then enter the following command:CONNECT /@database_alias
-
Note:
The challenge-response mode can be configured for all login cases.
Parent topic: Configuring RADIUS Authentication
22.6 RSA ACE/Server Configuration Checklist
If you are using an RSA ACE/Server RADIUS server, check the host agent and SecurID tokens for this server before making the initial connection.
-
Ensure that the host agent in the RSA ACE/Server is set up to send a node secret. In version 5.0, this is done by leaving the SENT Node secret box unchecked. If the RSA ACE/Server fails to send a node secret to the agent, then a node verification failure message will be written to the RSA ACE/Server log.
-
If you are using RSA SecurID tokens, then ensure that the token is synchronized with the RSA ACE/Server.
See Also:
RSA ACE/Server documentation for specific information about troubleshooting.
Parent topic: Configuring RADIUS Authentication