23 Configuring RADIUS Authentication
RADIUS is a client/server security protocol widely used to enable remote authentication and access.
- About Configuring RADIUS Authentication
An Oracle Database network can use any authentication method that supports the RADIUS standard. - RADIUS Components
RADIUS has a set of authentication components that enable you to manage configuration settings. - RADIUS Authentication Modes
User authentication can take place either through synchronous authentication mode or challenge-response (asynchronous) authentication mode. - Enabling RADIUS Authentication, Authorization, and Accounting
To enable RADIUS authentication, authorization, and accounting, you can use Oracle Net Manager. - Using RADIUS to Log in to a Database
You can use RADIUS to log into a database by using either synchronous authentication mode or challenge-response mode. - RSA ACE/Server Configuration Checklist
If you are using an RSA ACE/Server RADIUS server, check the host agent and SecurID tokens for this server before making the initial connection.
Parent topic: Managing Strong Authentication
23.1 About Configuring RADIUS Authentication
An Oracle Database network can use any authentication method that supports the RADIUS standard.
The supported RADIUS standard includes token cards and smart cards when you install and configure the RADIUS protocol. Oracle Database uses RADIUS in a client/server network environment. Moreover, when you use RADIUS, you can change the authentication method without modifying either the Oracle client or the Oracle database server.
From an end user's perspective, the entire authentication process is transparent. When the user seeks access to an Oracle database server, the Oracle database server, acting as the RADIUS client, notifies the RADIUS server. The RADIUS server then:
-
Looks up the user's security information
-
Passes authentication and authorization information between the appropriate authentication server or servers and the Oracle database server
-
Grants the user access to the Oracle database server
-
Logs session information, including when, how often, and for how long the user was connected to the Oracle database server
Note:
Oracle Database does not support RADIUS authentication over database links.
Figure 23-1 illustrates the Oracle Database-RADIUS environment.
Figure 23-1 RADIUS in an Oracle Environment
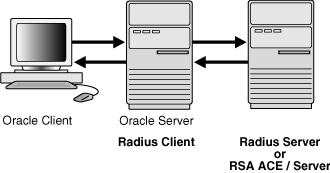
Description of "Figure 23-1 RADIUS in an Oracle Environment"
The Oracle Database server acts as the RADIUS client, passing information between the Oracle client and the RADIUS server. Similarly, the RADIUS server passes information between the Oracle database server and the appropriate authentication servers.
A RADIUS server vendor is often the authentication server vendor as well. In this case authentication can be processed on the RADIUS server. For example, the RSA ACE/Server is both a RADIUS server and an authentication server. It thus authenticates the user's pass code.
Note:
SecurID, an authentication product of RSA Security, Inc., though not directly supported by Oracle Database, has been certified as RADIUS-compliant. You can therefore, run SecurID under RADIUS. Refer to the RSA Security SecurID documentation for further information.Related Topics
Parent topic: Configuring RADIUS Authentication
23.2 RADIUS Components
RADIUS has a set of authentication components that enable you to manage configuration settings.
Table 23-1 lists the authentication components.
Table 23-1 RADIUS Authentication Components
| Component | Stored Information |
|---|---|
|
Oracle client |
Configuration setting for communicating through RADIUS. |
|
Oracle database server/RADIUS client |
Configuration settings for passing information between the Oracle client and the RADIUS server. The secret key file. |
|
RADIUS server |
Authentication and authorization information for all users. Each client's name or IP address. Each client's shared secret. Unlimited number of menu files enabling users already authenticated to select different login options without reconnecting. |
|
Authentication server or servers |
User authentication information such as pass codes and PINs, depending on the authentication method in use. Note: The RADIUS server can also be the authentication server. |
Parent topic: Configuring RADIUS Authentication
23.3 RADIUS Authentication Modes
User authentication can take place either through synchronous authentication mode or challenge-response (asynchronous) authentication mode.
- Synchronous Authentication Mode
In the synchronous mode, RADIUS lets you use various authentication methods, including passwords and SecurID token cards. - Challenge-Response (Asynchronous) Authentication Mode
When the system uses the asynchronous mode, the user does not need to enter a user name and password at the SQL*Plus CONNECT string.
Parent topic: Configuring RADIUS Authentication
23.3.1 Synchronous Authentication Mode
In the synchronous mode, RADIUS lets you use various authentication methods, including passwords and SecurID token cards.
- Sequence for Synchronous Authentication Mode
The sequence of synchronous authentication mode is comprised of six steps. - Example: Synchronous Authentication with SecurID Token Cards
With SecurID authentication, each user has a token card that displays a dynamic number that changes every sixty seconds.
Parent topic: RADIUS Authentication Modes
23.3.1.1 Sequence for Synchronous Authentication Mode
The sequence of synchronous authentication mode is comprised of six steps.
Figure 23-2 shows the sequence in which synchronous authentication occurs.
Figure 23-2 Synchronous Authentication Sequence
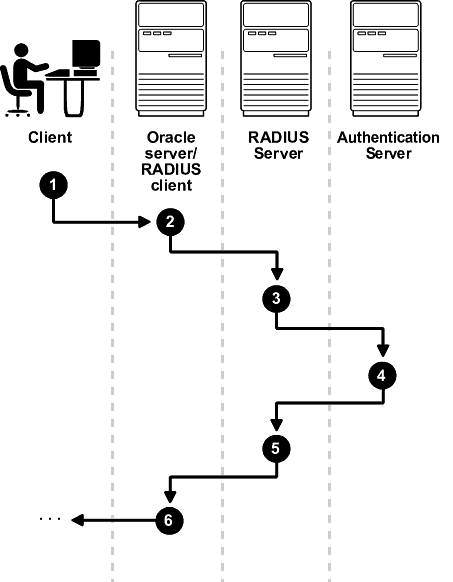
Description of "Figure 23-2 Synchronous Authentication Sequence"
The following steps describe the synchronous authentication sequence:
-
A user logs in by entering a connect string, pass code, or other value. The client system passes this data to the Oracle database server.
-
The Oracle database server, acting as the RADIUS client, passes the data from the Oracle client to the RADIUS server.
-
The RADIUS server passes the data to the appropriate authentication server, such as Smart Card or SecurID ACE for validation.
-
The authentication server sends either an Access Accept or an Access Reject message back to the RADIUS server.
-
The RADIUS server passes this response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client passes the response back to the Oracle client.
Parent topic: Synchronous Authentication Mode
23.3.1.2 Example: Synchronous Authentication with SecurID Token Cards
With SecurID authentication, each user has a token card that displays a dynamic number that changes every sixty seconds.
To gain access to the Oracle database server/RADIUS client, the user enters a valid pass code that includes both a personal identification number (PIN) and the dynamic number currently displayed on the user's SecurID card. The Oracle database server passes this authentication information from the Oracle client to the RADIUS server, which in this case is the authentication server for validation. Once the authentication server (RSA ACE/Server) validates the user, it sends an accept packet to the Oracle database server, which, in turn, passes it to the Oracle client. The user is now authenticated and able to access the appropriate tables and applications.
See Also:
Documentation provided by RSA Security, Inc.
Parent topic: Synchronous Authentication Mode
23.3.2 Challenge-Response (Asynchronous) Authentication Mode
When the system uses the asynchronous mode, the user does not need to enter a user name and password at the SQL*Plus CONNECT string.
- Sequence for Challenge-Response (Asynchronous) Authentication Mode
The sequence for challenge-response (asynchronous) authentication mode is comprised of 12 steps. - Example: Asynchronous Authentication with Smart Cards
With smart card authentication, the user logs in by inserting the smart card into a smart card reader that reads the smart card. - Example: Asynchronous Authentication with ActivCard Tokens
One particular ActivCard token is a hand-held device with a keypad and which displays a dynamic password.
Parent topic: RADIUS Authentication Modes
23.3.2.1 Sequence for Challenge-Response (Asynchronous) Authentication Mode
The sequence for challenge-response (asynchronous) authentication mode is comprised of 12 steps.
Figure 23-3 shows the sequence in which challenge-response (asynchronous) authentication occurs.
Note:
If the RADIUS server is the authentication server, Steps 3, 4, and 5, and Steps 9, 10, and 11 in Figure 23-3 are combined.
Figure 23-3 Asynchronous Authentication Sequence
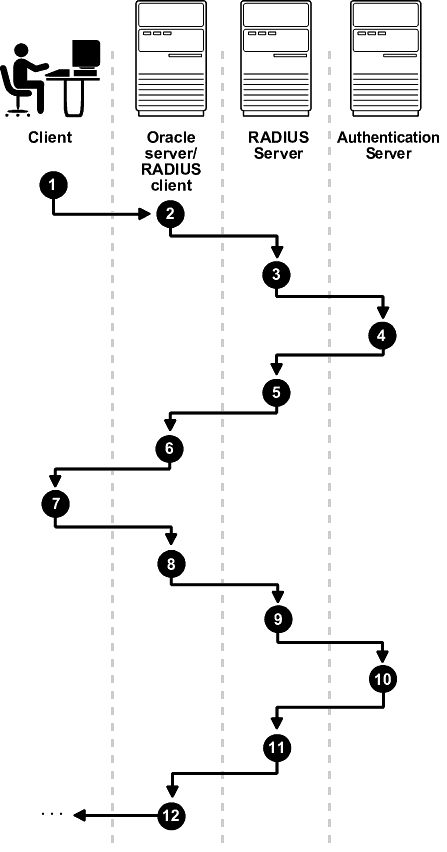
Description of "Figure 23-3 Asynchronous Authentication Sequence"
The following steps describe the asynchronous authentication sequence:
-
A user initiates a connection to an Oracle database server. The client system passes the data to the Oracle database server.
-
The Oracle database server, acting as the RADIUS client, passes the data from the Oracle client to the RADIUS server.
-
The RADIUS server passes the data to the appropriate authentication server, such as a Smart Card, SecurID ACE, or token card server.
-
The authentication server sends a challenge, such as a random number, to the RADIUS server.
-
The RADIUS server passes the challenge to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client, in turn, passes it to the Oracle client. A graphical user interface presents the challenge to the user.
-
The user provides a response to the challenge. To formulate a response, the user can, for example, enter the received challenge into the token card. The token card provides a dynamic password that is entered into the graphical user interface. The Oracle client passes the user's response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client sends the user's response to the RADIUS server.
-
The RADIUS server passes the user's response to the appropriate authentication server for validation.
-
The authentication server sends either an Access Accept or an Access Reject message back to the RADIUS server.
-
The RADIUS server passes the response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client passes the response to the Oracle client.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
23.3.2.2 Example: Asynchronous Authentication with Smart Cards
With smart card authentication, the user logs in by inserting the smart card into a smart card reader that reads the smart card.
The smart card is a plastic card, like a credit card, with an embedded integrated circuit for storing information.
The Oracle client sends the login information contained in the smart card to the authentication server by way of the Oracle database server/RADIUS client and the RADIUS server. The authentication server sends back a challenge to the Oracle client, by way of the RADIUS server and the Oracle database server, prompting the user for authentication information. The information could be, for example, a PIN as well as additional authentication information contained on the smart card.
The Oracle client sends the user's response to the authentication server by way of the Oracle database server and the RADIUS server. If the user has entered a valid number, the authentication server sends an accept packet back to the Oracle client by way of the RADIUS server and the Oracle database server. The user is now authenticated and authorized to access the appropriate tables and applications. If the user has entered incorrect information, the authentication server sends back a message rejecting user's access.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
23.3.2.3 Example: Asynchronous Authentication with ActivCard Tokens
One particular ActivCard token is a hand-held device with a keypad and which displays a dynamic password.
When the user seeks access to an Oracle database server by entering a password, the information is passed to the appropriate authentication server by way of the Oracle database server/RADIUS client and the RADIUS server. The authentication server sends back a challenge to the client, by way of the RADIUS server and the Oracle database server. The user types that challenge into the token, and the token displays a number for the user to send in response.
The Oracle client then sends the user's response to the authentication server by way of the Oracle database server and the RADIUS server. If the user has typed a valid number, the authentication server sends an accept packet back to the Oracle client by way of the RADIUS server and the Oracle database server. The user is now authenticated and authorized to access the appropriate tables and applications. If the user has entered an incorrect response, the authentication server sends back a message rejecting the user's access.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
23.4 Enabling RADIUS Authentication, Authorization, and Accounting
To enable RADIUS authentication, authorization, and accounting, you can use Oracle Net Manager.
- Step 1: Configure RADIUS Authentication
To configure RADIUS authentication, you must first configure it on the Oracle client, then the server. Afterward, you can configure additional RADIUS features. - Step 2: Create a User and Grant Access
After you complete the RADIUS authentication, you must create an Oracle Database user who for the RADIUS configuration. - Step 3: Configure External RADIUS Authorization (Optional)
You must configure the Oracle server, the Oracle client, and the RADIUS server to RADIUS users who must connect to an Oracle database. - Step 4: Configure RADIUS Accounting
RADIUS accounting logs information about access to the Oracle database server and stores it in a file on the RADIUS accounting server. - Step 5: Add the RADIUS Client Name to the RADIUS Server Database
The RADIUS server that you select must comply with RADIUS standards. - Step 6: Configure the Authentication Server for Use with RADIUS
After you add the RADIUS client name to the RADIUS server database, you can configure the authentication server to use the RADIUS. - Step 7: Configure the RADIUS Server for Use with the Authentication Server
After you configure the authentication server for use with RADIUS, you can configure the RADIUS server to use the authentication server. - Step 8: Configure Mapping Roles
If the RADIUS server supports vendor type attributes, then you can manage roles by storing them in the RADIUS server.
Parent topic: Configuring RADIUS Authentication
23.4.1 Step 1: Configure RADIUS Authentication
To configure RADIUS authentication, you must first configure it on the Oracle client, then the server. Afterward, you can configure additional RADIUS features.
Note:
Unless otherwise indicated, perform these configuration tasks by using Oracle Net Manager or by using any text editor to modify the sqlnet.ora file. Be aware that the settings in the sqlnet.ora file apply to all pluggable databases (PDBs).
- Step 1A: Configure RADIUS on the Oracle Client
You can use Oracle Net Manager to configure RADIUS on the Oracle client. - Step 1B: Configure RADIUS on the Oracle Database Server
You must create a file to hold the RADIUS key and store this file on the Oracle database server. Then you must configure the appropriate parameters in thesqlnet.orafile. - Step 1C: Configure Additional RADIUS Features
You can change the default settings, configure the challenge-response mode, and set parameters for an alternate RADIUS server.
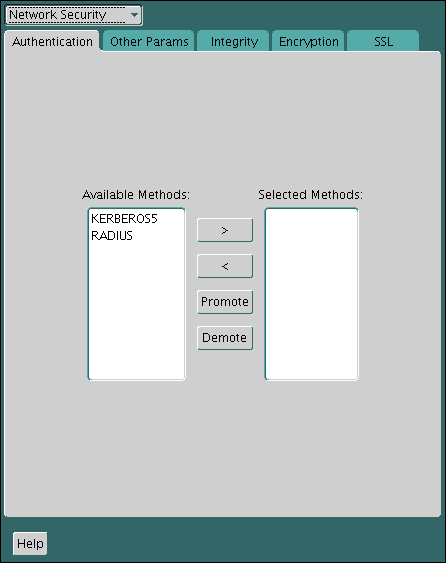
23.4.1.1 Step 1A: Configure RADIUS on the Oracle Client
You can use Oracle Net Manager to configure RADIUS on the Oracle client.
Parent topic: Step 1: Configure RADIUS Authentication
23.4.1.2 Step 1B: Configure RADIUS on the Oracle Database Server
You must create a file to hold the RADIUS key and store this file on the Oracle database server. Then you must configure the appropriate parameters in the sqlnet.ora file.
- Step 1B (1): Create the RADIUS Secret Key File on the Oracle Database Server
First, you must create the RADIUS secret key file. - Step 1B (2): Configure RADIUS Parameters on the Server (sqlnet.ora file)
After you create RADIUS secret key file, you are ready to configure the appropriate parameters in thesqlnet.orafile. - Step 1B (3): Set Oracle Database Server Initialization Parameters
After you configure thesqlnet.orafile, you must configure theinit.orainitialization file.
Parent topic: Step 1: Configure RADIUS Authentication
23.4.1.2.1 Step 1B (1): Create the RADIUS Secret Key File on the Oracle Database Server
First, you must create the RADIUS secret key file.
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
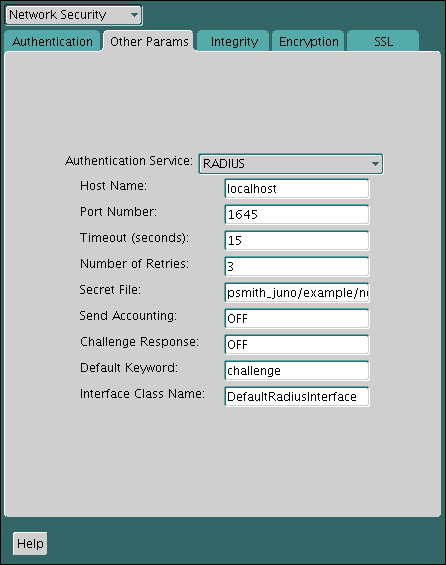
23.4.1.2.2 Step 1B (2): Configure RADIUS Parameters on the Server (sqlnet.ora file)
After you create RADIUS secret key file, you are ready to configure the appropriate parameters in the sqlnet.ora file.
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
23.4.1.2.3 Step 1B (3): Set Oracle Database Server Initialization Parameters
After you configure the sqlnet.ora file, you must configure the init.ora initialization file.
Related Topics
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
23.4.1.3 Step 1C: Configure Additional RADIUS Features
You can change the default settings, configure the challenge-response mode, and set parameters for an alternate RADIUS server.
- Step 1C(1): Change Default Settings
You can use Oracle Net Manager to change the default RADIUS settings. - Step 1C(2): Configure Challenge-Response Mode
To configure challenge-response mode, you must specify information such as a dynamic password that you obtain from a token card. - Step 1C(3): Set Parameters for an Alternate RADIUS Server
If you are using an alternate RADIUS server, then you must set additional parameters.
Parent topic: Step 1: Configure RADIUS Authentication
23.4.1.3.1 Step 1C(1): Change Default Settings
You can use Oracle Net Manager to change the default RADIUS settings.
23.4.1.3.2 Step 1C(2): Configure Challenge-Response Mode
To configure challenge-response mode, you must specify information such as a dynamic password that you obtain from a token card.
Related Topics
Parent topic: Step 1C: Configure Additional RADIUS Features
23.4.1.3.3 Step 1C(3): Set Parameters for an Alternate RADIUS Server
If you are using an alternate RADIUS server, then you must set additional parameters.
Parent topic: Step 1C: Configure Additional RADIUS Features
23.4.2 Step 2: Create a User and Grant Access
After you complete the RADIUS authentication, you must create an Oracle Database user who for the RADIUS configuration.
See Also:
Administration documentation for the RADIUS server
23.4.3 Step 3: Configure External RADIUS Authorization (Optional)
You must configure the Oracle server, the Oracle client, and the RADIUS server to RADIUS users who must connect to an Oracle database.
- Step 3A: Configure the Oracle Server (RADIUS Client)
You can edit theinit.orafile to configure an Oracle server for a RADIUS client. - Step 3B: Configure the Oracle Client Where Users Log In
Next, you must configure the Oracle client where users log in. - Step 3C: Configure the RADIUS Server
To configure the RADIUS server, you must modify the RADIUS server attribute configuration file.
23.4.3.1 Step 3A: Configure the Oracle Server (RADIUS Client)
You can edit the init.ora file to configure an Oracle server for a RADIUS client.
init.ora file, restart the database, and the set the RADIUS challenge-response mode.
Related Topics
23.4.3.2 Step 3B: Configure the Oracle Client Where Users Log In
Next, you must configure the Oracle client where users log in.
- Set the RADIUS challenge-response mode to
ONfor the client if you have not already done so.
Related Topics
23.4.4 Step 4: Configure RADIUS Accounting
RADIUS accounting logs information about access to the Oracle database server and stores it in a file on the RADIUS accounting server.
Use this feature only if both the RADIUS server and authentication server support it.
- Step 4A: Set RADIUS Accounting on the Oracle Database Server
To set RADIUS accounting on the server, you can use Oracle Net Manager. - Step 4B: Configure the RADIUS Accounting Server
RADIUS Accounting Server resides on the same host as the RADIUS authentication server or on a separate host.
23.4.4.1 Step 4A: Set RADIUS Accounting on the Oracle Database Server
To set RADIUS accounting on the server, you can use Oracle Net Manager.
Parent topic: Step 4: Configure RADIUS Accounting
23.4.4.2 Step 4B: Configure the RADIUS Accounting Server
RADIUS Accounting Server resides on the same host as the RADIUS authentication server or on a separate host.
- See the administration documentation for the RADIUS server, for information about configuring RADIUS accounting.
Parent topic: Step 4: Configure RADIUS Accounting
23.4.5 Step 5: Add the RADIUS Client Name to the RADIUS Server Database
The RADIUS server that you select must comply with RADIUS standards.
See Also:
Administration documentation for the RADIUS server
23.4.6 Step 6: Configure the Authentication Server for Use with RADIUS
After you add the RADIUS client name to the RADIUS server database, you can configure the authentication server to use the RADIUS.
- Refer to the authentication server documentation for instructions about configuring the authentication servers.
23.4.7 Step 7: Configure the RADIUS Server for Use with the Authentication Server
After you configure the authentication server for use with RADIUS, you can configure the RADIUS server to use the authentication server.
- Refer to the RADIUS server documentation for instructions about configuring the RADIUS server for use with the authentication server.
23.4.8 Step 8: Configure Mapping Roles
If the RADIUS server supports vendor type attributes, then you can manage roles by storing them in the RADIUS server.
CONNECT request using RADIUS.To use this feature, you must configure roles on both the Oracle database server and the RADIUS server.
23.5 Using RADIUS to Log in to a Database
You can use RADIUS to log into a database by using either synchronous authentication mode or challenge-response mode.
Parent topic: Configuring RADIUS Authentication
23.6 RSA ACE/Server Configuration Checklist
If you are using an RSA ACE/Server RADIUS server, check the host agent and SecurID tokens for this server before making the initial connection.
-
Ensure that the host agent in the RSA ACE/Server is set up to send a node secret. In version 5.0, this is done by leaving the SENT Node secret box unchecked. If the RSA ACE/Server fails to send a node secret to the agent, then a node verification failure message will be written to the RSA ACE/Server log.
-
If you are using RSA SecurID tokens, then ensure that the token is synchronized with the RSA ACE/Server.
See Also:
RSA ACE/Server documentation for specific information about troubleshooting.
Parent topic: Configuring RADIUS Authentication